Too Cool For Unique IDs
The PyPi repository, properly called the Python Package Index delivers community developed Python applications and packages to anyone who needs them. It is similar to GitHub in that anyone can launch and track a project on PyPi and anyone can use the pip command to download and install those packages. While it isn’t as popular on Windows as it is on Linux based machines it currently hosts 564,840 packages, the most popular of which see millions of downloads each day. That makes it a perfect target for bad actors and we have certainly seen them successfully use it to spread malware in the past. This might cause you to assume PyPi would include one of the most basic of security features; however you know what they say about assumptions.
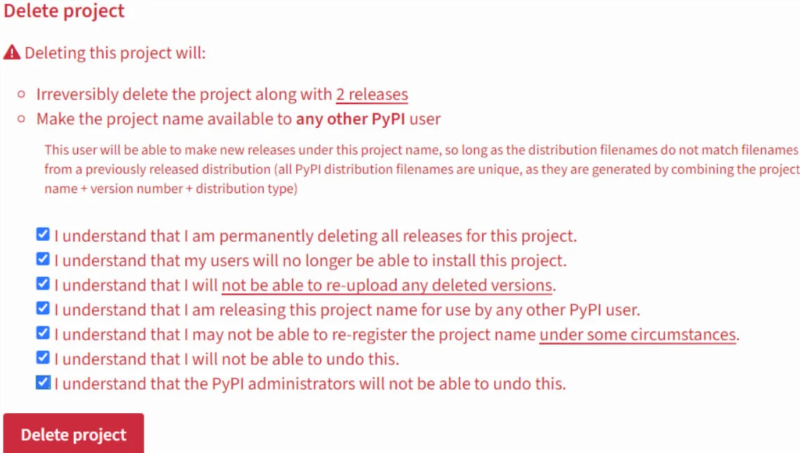
A new attack vector has been discovered, dubbed the Revival Hijack and it takes advantage of the fact that PyPi does not assign one of the most basic unique attributes you could assign to a package to ensure it is what it says it is. A PyPi package’s name is not protected in any way, so if someone abandons a project for any reason whatsoever and deletes it from the database, anyone else can create a package with the same name and pip has no way to know that it has changed. In most scenarios, you might have duplicate project or user names but each and every one is assigned a unique ID so that if one is deleted and later replaced with a new user or project of the same name, the unique ID is different so that systems can tell the difference.
Bleeping Computer posted research from JFrog that proves an attacker can wait for a project to be deleted and then immediately create a new project with the same name, filled with whatever code they feel like, and pip will happily download and install it. PyPI does maintains a non-public blocklist, but there is no guarantee that a deleted project will be added to prevent an attack like the Revival Hijack from occurring. This has been noticed by the black hats and has indeed been taken advatage of.
You can thank JFrog for being proactive and registering a number of deleted projects under the name security_holding; they may not maintain the previous packages but they will prevent someone from bringing them back with modified code. Short of being the developer or being intimately familiar with the pending deletion of a project there is little you can do to protect yourself.
We await word on if PyPi intends to change this.