It’s Not Unpatchable, But The Performance Impact Would Be Massive
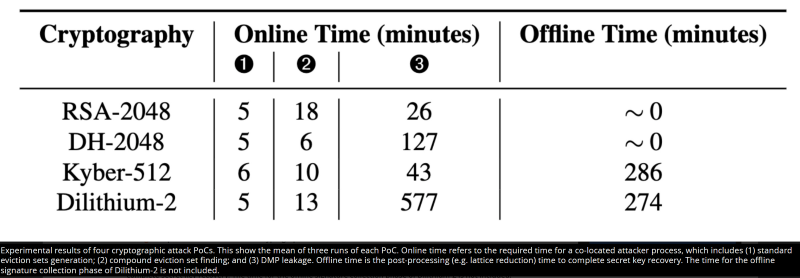
Proud owners of a M1, M2 or M3 based Apple devices are not having a good day. The newly revealed GoFetch attack is worrying enough to ruin a perfectly good Friday as it allows attackers to steal secret cryptographic keys from your system. To make things even worse, the vulnerability doesn’t require root access to leverage, all it needs is the same level of access any third party app does to be able to start stealing keys. The time it takes is not encouraging, for instance it takes less than an hour to extract a 2048-bit RSA key and a little over two hours to extract a 2048-bit Diffie-Hellman key.
The vulnerability comes from Apple’s decision to not follow standard practice when designing the data memory-dependent prefetchers in their M series of chips. GoFetch has been described as unpatchable, which is true for the M1 and M2 but not the M3. There are ways to mitigate the vulnerability however much like Spectre and the like which Intel and AMD processors are vulnerable to, patching will have a seriously negative effect on performance. The articles at Bleeping Computer and Ars Technica don’t specify just how large that impact will be on the M3’s performance, likely because it hasn’t been full tested yet, but it will likely be very large.
Keep an eye out for more news, and be very careful what apps you install on your new Mac.